web入门操作
# PREFACE:
# curl
- curl 发送 get 指令
curl 127.0.0.1 -p 80
注意 url 编码
添加 header
curl 127.0.0.1 -p 80 --header “Host:40bb89ca76728698378750073647169d”
注意转义
curl 127.0.0.1?a=963fe9d3ff95f80bff64f57c210a739f
\&b=f8e12324%202bbd1304%2634341212%231eebbb9b
POST data:
curl 127.0.0.1 -d a=5129ddc180c847f3788d5493e2fdea93
发送 json(json 内不需要转义)
curl 127.0.0.1:80 -H “Content-Type:application/json” -d ‘{“a”:“17aa707fc88e62cab3cf40403d43e025”,“b”:{“c”:“6869f0a6”,“d”:[“193c021a”,“1de1e1a0 9384ce04&8ae5cbbb#6
eabcff1”]}}’
重定向
curl 127.0.0.1 --location-trusted
获取 cookie
curl -c - 127.0.0.1:80
发送 cookie
curl --cookie 71ed1a72ed58d7146e2798f2945a11dc 127.0.0.1
# nc
- nc 发送 get 指令
printf “GET /index.html HTTP/1.1\r\nUser-Agent: nc/0.0.1\r\nHost: 127.0.0.1\r\nAccept: /\r\n\r\n” | nc 127.0.0.1 80
注意:更改为其他 input 方式,否则 url 编码会过不了
hacker@talking-web~level14:/$ nc 127.0.0.1 80
GET /index.html?a=a1834ce5ff3a8434e97e721b647e84a0 HTTP/1.1
可以:nc 127.0.0.1 80 < exp.txt
tips: 这里 nc 会自动把 \n 处理成 \r\n
POST / HTTP/1.1
Host: 127.0.0.1:80
Content-Type: application/x-www-form-urlencoded; charset=utf-8
Content-Length: 34
a=b7f875a1d22f3884e72c830ccd2dae79
POST / HTTP/1.1
Host: 127.0.0.1:80
Content-Type: application/json
Content-Length: 40
{"a":"fb1fcbc678ea9ab1c60e7d89291a6ad0"}
nc 信任重定向
cookie:
POST /08ef55da8a1e676feea750320e3b0942 HTTP/1.1
Host: 127.0.0.1
Content-Type: application/json
Content-Length: 116
Cookie: cookie=c106c3a4d0d7620eee3b2cd121ff77ec
Referer: 127.0.0.1
# python
- python 发送 get(不需要 url 编码)
import requests | |
headers = { | |
'Host':"71da60ef1b789332773275354004e689", | |
} | |
response = requests.post("http://127.0.0.1:80",params={"a":"62e9fb4ed3b5fafd87b163b3a20fef5b","b":"93db500a 663544b4&c0fa24b2#5b3824c1"},headers=headers) | |
print(response.text) |
- post
import requests | |
import json | |
data = {"a":"fb7a58692e22a3fc71c5017aa0541b00"} | |
headers = { | |
'Host':"71da60ef1b789332773275354004e689", | |
"Content-Type":"application/x-www-form-urlencoded; charset=utf-8", | |
} | |
response = requests.post("http://127.0.0.1:80",data=data,headers=headers) | |
print(response.text) |
json
import requests | |
import json | |
data = {"a":"cb449746a07887172af1ad3bc700d7cc","b":"6b0e7b4b 208ac3c8&2a6652a6#b948b54f"} | |
data = json.dumps(data) | |
headers = { | |
'Host':"71da60ef1b789332773275354004e689", | |
"Content-Type":"application/json", | |
} | |
response = requests.post("http://127.0.0.1:80",data=data,headers=headers) | |
print(response.text) |
Python 自动重定向
Python 不需要手动维护 cookie
# web syscall
network system calls are mostly big endian
ip protocol socket:
socket(AF_INET, SOCK_STREAM, IPPROTO_IP)
mov rdi, 2
mov rsi, 1
mov rdx, 0
mov rax, 41
syscall
bind:
bind(3, {sa_family=AF_INET, sin_port=htons(80), sin_addr=inet_addr(“0.0.0.0”)}, 16)
sub rsp, 4
mov word ptr [rsp], 2
mov word ptr [rsp + 3], 80
mov dword ptr [rsp + 4], 0x00000000
push rsp
pop rsi
mov rdi, rax
mov rdx, 16
mov rax, 49
syscall
accept
accept(3, NULL, NULL)
mov rdi, 3
xor rsi, rsi
xor rdx, rdx
mov rax, 43
syscall
进行接收 & 回包
[✓] execve(“/proc/self/fd/3”, [“/proc/self/fd/3”], 0x7f0eeb6ad980 /* 0 vars */) = 0
[✓] socket(AF_INET, SOCK_STREAM, IPPROTO_IP) = 3
[✓] bind(3, {sa_family=AF_INET, sin_port=htons(80), sin_addr=inet_addr(“0.0.0.0”)}, 16) = 0
[✓] listen(3, 0) = 0
[✓] accept(3, NULL, NULL) = 4
[✓] read(4, “GET / HTTP/1.1\r\nHost: localhost\r\nUser-Agent: python-requests/2.31.0\r\nAccept-Encoding: gzip, deflate, zstd\r\nAccept: /\r\nConnection: keep-alive\r\n\r\n”, 10000) = 146
[✓] write(4, “HTTP/1.0 200 OK\r\n\r\n”, 19) = 19
[✓] close(4) = 0
[✓] exit(0) = ?
.intel_syntax noprefix
.globl _start
.section .text
_start:
mov rdi, 2
mov rsi, 1
mov rdx, 0
mov rax, 41
syscall
sub rsp, 4
mov word ptr [rsp], 2
mov word ptr [rsp + 3], 80
mov dword ptr [rsp + 4], 0x00000000
push rsp
pop rsi
mov rdi, rax
mov rdx, 16
mov rax, 49
syscall
mov rdi, 3
mov rsi, 0
mov rax, 50
syscall
mov rdi, 3
xor rsi, rsi
xor rdx, rdx
mov rax, 43
syscall
mov rdi, 4
push rsp
pop rsi
mov rdx, 10000
xor rax, rax
syscall
sub rsp, 19
mov dword ptr [rsp], 0x50545448
mov dword ptr [rsp + 4], 0x302e312f
mov dword ptr [rsp + 8], 0x30303220
mov dword ptr [rsp + 12], 0x0d4b4f20
mov qword ptr [rsp + 16], 0xa0d0a
push rsp
pop rsi
mov rdx, 19
mov rax, 1
syscall
mov rdi, 4
mov rax, 3
syscall
mov rdi, 0
mov rax, 60
syscall
根据接包进行 get 请求:
.intel_syntax noprefix
.globl _start
.section .text
_start:
mov rdi, 3
mov rax, 3
syscall
mov rdi, 2
mov rsi, 1
mov rdx, 0
mov rax, 41
syscall
sub rsp, 4
mov word ptr [rsp], 2
mov word ptr [rsp + 3], 80
mov dword ptr [rsp + 4], 0x00000000
push rsp
pop rsi
mov rdi, rax
mov rdx, 16
mov rax, 49
syscall
mov rdi, 3
mov rsi, 0
mov rax, 50
syscall
mov rdi, 3
xor rsi, rsi
xor rdx, rdx
mov rax, 43
syscall
//fork
mov rax, 57
syscall
// read
mov rdi, 4
push rsp
pop rsi
mov rdx, 10000
xor rax, rax
syscall
mov rcx, rsp
add rcx, 4
// open
sub rsp, 9
mov byte ptr [rsp], 0x2e
mov byte ptr [rsp + 1], 0x2f
mov byte ptr [rsp + 2], 0x65
mov byte ptr [rsp + 3], 0x78
mov byte ptr [rsp + 4], 0x70
mov byte ptr [rsp + 5], 0x2e
mov byte ptr [rsp + 6], 0x74
mov byte ptr [rsp + 7], 0x78
mov byte ptr [rsp + 8], 0x74
mov byte ptr [rsp + 9], 0x00
push rcx
mov byte ptr [rcx + 16], 0x00
pop rdi
mov rsi, 0
mov rax, 2
syscall
// read
mov rdi, rax
mov rsi, rsp
mov rdx, 202
mov rax, 0
syscall
mov r8, rax
// close
mov rsi, 5
mov rax, 3
syscall
// write
mov rdi, 4
sub rsp, 24
mov dword ptr [rsp], 0x50545448
mov dword ptr [rsp + 4], 0x302e312f
mov dword ptr [rsp + 8], 0x30303220
mov dword ptr [rsp + 12], 0x0d4b4f20
mov qword ptr [rsp + 16], 0x000a0d0a
push rsp
pop rsi
mov rdx, 19
mov rax, 1
syscall
add rsp, 24
// write
mov rdi, 4
mov rsi, rsp
mov rdx, r8
mov rax, 1
syscall
// close
mov rdi, 4
mov rax, 3
syscall
// accept
mov rdi, 3
xor rsi, rsi
xor rdx, rdx
mov rax, 43
syscall
.intel_syntax noprefix
.globl _start
.section .text
_start:
mov rdi, 2
mov rsi, 1
mov rdx, 0
mov rax, 41
syscall
sub rsp, 4
mov word ptr [rsp], 2
mov word ptr [rsp + 3], 80
mov dword ptr [rsp + 4], 0x00000000
push rsp
pop rsi
mov rdi, rax
mov rdx, 16
mov rax, 49
syscall
mov rdi, 3
mov rsi, 0
mov rax, 50
syscall
// accept
mov rdi, 3
xor rsi, rsi
xor rdx, rdx
mov rax, 43
syscall
mov r8, rax
//fork
mov rax, 57
syscall
// close
mov rdi, r8
mov rax, 3
syscall
// accept
mov rdi, 3
xor rsi, rsi
xor rdx, rdx
mov rax, 43
syscall
循环开线程接包发包 get
========= Parent Process ==========
[ ] execve(<execve_args>) = 0
[ ] socket(AF_INET, SOCK_STREAM, IPPROTO_IP) = 3
[ ] bind(3, {sa_family=AF_INET, sin_port=htons(<bind_port>), sin_addr=inet_addr("<bind_address>")}, 16) = 0
- Bind to port 80
- Bind to address 0.0.0.0
[ ] listen(3, 0) = 0
[ ] accept(3, NULL, NULL) = 4
[ ] fork() = <fork_result>
[ ] close(4) = 0
[ ] accept(3, NULL, NULL) = ?
========= Child Process ==========
[ ] close(3) = 0
[ ] read(4, <read_request>, <read_request_count>) = <read_request_result>
[ ] open("<open_path>", O_RDONLY) = 3
[ ] read(3, <read_file>, <read_file_count>) = <read_file_result>
[ ] close(3) = 0
[ ] write(4, "HTTP/1.0 200 OK\r\n\r\n", 19) = 19
[ ] write(4, <write_file>, <write_file_count>) = <write_file_result>
[ ] exit(0) = ?
.intel_syntax noprefix
.globl _start
.section .text
_start:
parent:
// socket
mov rdi, 2
mov rsi, 1
mov rdx, 0
mov rax, 41
syscall
// bind
sub rsp, 4
mov word ptr [rsp], 2
mov word ptr [rsp + 3], 80
mov dword ptr [rsp + 4], 0x00000000
push rsp
pop rsi
mov rdi, rax
mov rdx, 16
mov rax, 49
syscall
// listen
mov rdi, 3
mov rsi, 0
mov rax, 50
syscall
// accept
mov rdi, 3
xor rsi, rsi
xor rdx, rdx
mov rax, 43
syscall
mov r8, rax
//fork
mov rax, 57
syscall
cmp rax, 0
jz child
// close
mov rdi, 4
mov rax, 3
syscall
jmp parent
// accept
mov rdi, 3
xor rsi, rsi
xor rdx, rdx
mov rax, 43
syscall
child:
// close
mov rdi, 3
mov rax, 3
syscall
// read
mov rdi, 4
push rsp
pop rsi
mov rdx, 10000
xor rax, rax
syscall
mov rcx, rsp
add rcx, 4
// open
sub rsp, 9
mov byte ptr [rsp], 0x2e
mov byte ptr [rsp + 1], 0x2f
mov byte ptr [rsp + 2], 0x65
mov byte ptr [rsp + 3], 0x78
mov byte ptr [rsp + 4], 0x70
mov byte ptr [rsp + 5], 0x2e
mov byte ptr [rsp + 6], 0x74
mov byte ptr [rsp + 7], 0x78
mov byte ptr [rsp + 8], 0x74
mov byte ptr [rsp + 9], 0x00
push rcx
mov byte ptr [rcx + 16], 0x00
pop rdi
mov rsi, 0
mov rax, 2
syscall
// read
mov rdi, rax
mov rsi, rsp
mov rdx, 202
mov rax, 0
syscall
mov r8, rax
// close
mov rsi, 5
mov rax, 3
syscall
// write
mov rdi, 4
sub rsp, 24
mov dword ptr [rsp], 0x50545448
mov dword ptr [rsp + 4], 0x302e312f
mov dword ptr [rsp + 8], 0x30303220
mov dword ptr [rsp + 12], 0x0d4b4f20
mov qword ptr [rsp + 16], 0x000a0d0a
push rsp
pop rsi
mov rdx, 19
mov rax, 1
syscall
add rsp, 24
// write
mov rdi, 4
mov rsi, rsp
mov rdx, r8
mov rax, 1
syscall
// accept
mov rdi, 3
xor rsi, rsi
xor rdx, rdx
mov rax, 43
syscall
mov rdi, 0
mov rax, 60
syscall
post 接收参数并写入文件
.intel_syntax noprefix
.globl _start
.section .text
_start:
parent:
// socket
mov rdi, 2
mov rsi, 1
mov rdx, 0
mov rax, 41
syscall
// bind
sub rsp, 4
mov word ptr [rsp], 2
mov word ptr [rsp + 3], 80
mov dword ptr [rsp + 4], 0x00000000
push rsp
pop rsi
mov rdi, rax
mov rdx, 16
mov rax, 49
syscall
// listen
mov rdi, 3
mov rsi, 0
mov rax, 50
syscall
// accept
mov rdi, 3
xor rsi, rsi
xor rdx, rdx
mov rax, 43
syscall
mov r8, rax
//fork
mov rax, 57
syscall
cmp rax, 0
jz child
// close
mov rdi, 4
mov rax, 3
syscall
// accept
mov rdi, 3
xor rsi, rsi
xor rdx, rdx
mov rax, 43
syscall
jmp parent
child:
// close
mov rdi, 3
mov rax, 3
syscall
// read
mov rdi, 4
push rsp
pop rsi
mov rdx, 10000
xor rax, rax
syscall
mov r9, rsp
add r9, 5
mov r8, rax
// open
sub rsp, 9
push r9
mov byte ptr [r9 + 16], 0x00
pop rdi
mov rsi, 65
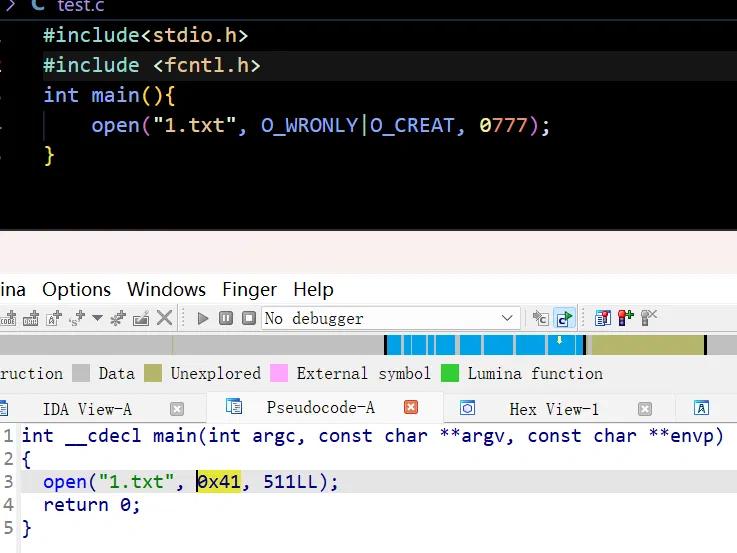
// 这里是八进制......
mov rdx, 511
mov rax, 2
syscall
// write
mov rdi, rax
add r9, 178
mov rsi, r9
mov rdx, r8
sub rdx, 183
mov rax, 1
syscall
// close
mov rsi, 3
mov rax, 3
syscall
// write
mov rdi, 4
sub rsp, 24
mov dword ptr [rsp], 0x50545448
mov dword ptr [rsp + 4], 0x302e312f
mov dword ptr [rsp + 8], 0x30303220
mov dword ptr [rsp + 12], 0x0d4b4f20
mov qword ptr [rsp + 16], 0x000a0d0a
push rsp
pop rsi
mov rdx, 19
mov rax, 1
syscall
add rsp, 24
// exit
mov rdi, 0
mov rax, 60
syscall
最终版 orz,整合了前面几个操作支持 get、post
.intel_syntax noprefix
.globl _start
.section .text
_start:
// socket
mov rdi, 2
mov rsi, 1
mov rdx, 0
mov rax, 41
syscall
mov rbx, rax
// bind
sub rsp, 4
mov word ptr [rsp], 2
mov word ptr [rsp + 3], 80
mov dword ptr [rsp + 4], 0x00000000
push rsp
pop rsi
mov rdi, rax
mov rdx, 16
mov rax, 49
syscall
// listen
mov rdi, rbx
mov rsi, 0
mov rax, 50
syscall
parent:
// accept
mov rdi, rbx
xor rsi, rsi
xor rdx, rdx
mov rax, 43
syscall
mov r13, rax
//fork
mov rax, 57
syscall
cmp rax, 0
jz child
// close
mov rdi, r13
mov rax, 3
syscall
// accept
// mov rdi, rbx
// xor rsi, rsi
// xor rdx, rdx
// mov rax, 43
// syscall
jmp parent
child:
// close
mov rdi, rbx
mov rax, 3
syscall
// read
mov rdi, r13
push rsp
pop rsi
mov rdx, 10000
xor rax, rax
syscall
mov r15, rax
mov r14, rsp
// 'P'
cmp byte ptr [r14], 80
jz post
get:
// open
sub rsp, 9
add r14, 4
push r14
mov byte ptr [r14 + 16], 0x00
pop rdi
mov rsi, 0
mov rdx, 0
mov rax, 2
syscall
// read
mov rdi, rax
mov rsi, rsp
mov rdx, 10000
mov rax, 0
syscall
mov r12, rax
// close
mov rax, 3
syscall
// write
mov rdi, r13
sub rsp, 24
mov dword ptr [rsp], 0x50545448
mov dword ptr [rsp + 4], 0x302e312f
mov dword ptr [rsp + 8], 0x30303220
mov dword ptr [rsp + 12], 0x0d4b4f20
mov qword ptr [rsp + 16], 0x000a0d0a
push rsp
pop rsi
mov rdx, 19
mov rax, 1
syscall
add rsp, 24
// write
mov rdi, r13
mov rsi, rsp
mov rdx, r12
mov rax, 1
syscall
mov rdi, 0
mov rax, 60
syscall
post:
add r14, 5
// open
sub rsp, 9
push r14
mov byte ptr [r14 + 16], 0x00
pop rdi
mov rsi, 65
// 这里是八进制......
mov rdx, 511
mov rax, 2
syscall
// write
mov rdi, rax
mov rdx, r15
sub rdx, 183
cmp rdx, 99
jg addOne
add rdx, 1
sub r14, 1
addOne:
add r14, 178
mov rsi, r14
mov rax, 1
syscall
// close
mov rsi, rbx
mov rax, 3
syscall
// write
mov rdi, r13
sub rsp, 24
mov dword ptr [rsp], 0x50545448
mov dword ptr [rsp + 4], 0x302e312f
mov dword ptr [rsp + 8], 0x30303220
mov dword ptr [rsp + 12], 0x0d4b4f20
mov qword ptr [rsp + 16], 0x000a0d0a
push rsp
pop rsi
mov rdx, 19
mov rax, 1
syscall
add rsp, 24
// exit
mov rdi, 0
mov rax, 60
syscall
# nc
连接
nc 127.0.0.1 80
接听
nc -lp 80
多线程扫描
import socket | |
import threading | |
def check_port(hostname, port): | |
try: | |
print(f'testing:{hostname}') | |
sock=socket.socket(socket.AF_INET,socket.SOCK_STREAM) | |
sock.settimeout(2) | |
result=sock.connect_ex((hostname,port)) | |
if (result == 0): | |
print(f'{hostname}----------') | |
sock.close() | |
except: | |
pass | |
for i in range(256): | |
try: | |
t = threading.Thread(target=check_port,args=(f'10.0.0.{i}',31337)) | |
t.start() | |
except: | |
print("Error: unable to start thread") | |
while 1: | |
pass |
更好的多线程扫描
import socket | |
import logging | |
from concurrent.futures import ProcessPoolExecutor, as_completed | |
# 配置日志 | |
logging.basicConfig(filename='port_check.log', level=logging.INFO, format='%(asctime)s - %(message)s') | |
def check_port(hostname, port): | |
# print(hostname) | |
# print(port) | |
try: | |
# logging.info(f'testing: {hostname}') | |
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM) | |
sock.settimeout(2) | |
result = sock.connect_ex((hostname, port)) | |
if result == 0: | |
logging.info(f'{hostname}----------') | |
return True | |
sock.close() | |
except: | |
pass | |
return False | |
def parallel_process(array, function): | |
""" | |
A parallel version of the map function with a progress bar. | |
Args: | |
array (array-like): An array to iterate over. | |
function (function): A python function to apply to the elements of array | |
Returns: | |
[function(array[0]), function(array[1]), ...] | |
""" | |
n_jobs = 512 # 线程数 | |
with ProcessPoolExecutor(max_workers=n_jobs) as pool: | |
futures = [pool.submit(function, *a) for a in array] # 使用 *a 解包参数元组 | |
kwargs = { | |
'total': len(futures), | |
'unit': 'it', | |
'unit_scale': True, | |
'leave': True | |
} | |
# Print out the progress as tasks complete | |
if __name__ == '__main__': | |
array = [(f'10.0.{j}.{i}', 31337) for i in range(256) for j in range(256)] # 构造参数数组 | |
# array = [(f'192.168.0.{i}', 31337) for i in range(256)] | |
# print(array) | |
res = parallel_process(array, check_port) |
# tcpdump 劫持
tcpdump -i any port 31337 -w capture.pcap
# hijack
增加 ip 监听以获取包
ip addr add 10.0.0.2 dev eth0
scapy 用法
Usage — Scapy 2.5.0 documentation
一些可用的指令:
ip route show
ip route add default via 10.0.0.1
广播 Ethernet 包(srp1 注意增加 filter,这样不会收到自己发的包,或者用 srp 批量都接收)
from scapy.all import * | |
# Get your MAC address (assuming you're on a Linux system) | |
# Create the Ethernet frame with your MAC address as the source | |
eth_frame = Ether(src="e6:d2:90:8f:34:8f", dst="ff:ff:ff:ff:ff:ff", type=0xFFFF) | |
# Send the Ethernet frame and receive packets | |
reply_packets = srp1(eth_frame, timeout=2, iface="eth0", filter="ether src not e6:d2:90:8f:34:8f") | |
# Display received packets | |
if reply_packets: | |
print(reply_packets.show()) | |
else: | |
print("No reply received.") |
发送 ip 包(注意,这里是一层一层搭建的,每层的包正常运转下一层的包才能成功发送,!注意!前面的 type 不能指定,这里是自动对 field 适应的,指定后会导致后续上层信息丢包)
from scapy.all import * | |
eth_frame = Ether(src="3e:72:ce:70:a9:74", dst="ff:ff:ff:ff:ff:ff") | |
ip_packet = IP(proto=0xFF, dst="10.0.0.3",src="10.0.0.2") | |
packet = eth_frame/ip_packet | |
reply_packets = srp1(packet, timeout=2, iface="eth0") | |
if reply_packets: | |
print(reply_packets.show()) | |
else: | |
print("No reply received.") |
发送 tcp 包,和上面一样的注意事项就一遍过
from scapy.all import * | |
eth_frame = Ether(src="02:42:0a:00:b5:ef", dst="ff:ff:ff:ff:ff:ff") | |
ip_packet = IP(dst="10.0.0.3",src="10.0.181.239") | |
tcp_packet = TCP(sport=31337, dport=31337, seq=31337, ack=31337, flags="APRSF") | |
packet = eth_frame/ip_packet/tcp_packet | |
reply_packets = srp1(packet, timeout=2, iface="eth0") | |
if reply_packets: | |
print(reply_packets.show()) | |
else: | |
print("No reply received.") |
官网的 demo: a=Ether()/IP(dst="www.slashdot.org")/TCP()/"GET /index.html HTTP/1.0 \n\n"
TCP handshake:
from scapy.all import * | |
eth_frame = Ether(src="8a:c9:61:2b:94:3c", dst="ff:ff:ff:ff:ff:ff") | |
ip_packet = IP(dst="10.0.0.3",src="10.0.0.2") | |
tcp_packet = TCP(sport=31337, dport=31337, seq=31337, flags="S") | |
packet = eth_frame/ip_packet/tcp_packet | |
reply_packets = srp1(packet, timeout=2, iface="eth0") | |
if reply_packets: | |
print(reply_packets.show()) | |
else: | |
print("No reply received.") | |
eth_frame = Ether(src="8a:c9:61:2b:94:3c", dst="ff:ff:ff:ff:ff:ff") | |
ip_packet = IP(dst="10.0.0.3",src="10.0.0.2") | |
tcp_packet = TCP(sport=31337, dport=31337, seq=31338, ack = reply_packets.seq + 1, flags="A") | |
packet = eth_frame/ip_packet/tcp_packet | |
reply_packets = srp1(packet, timeout=3, iface="eth0") | |
if reply_packets: | |
print(reply_packets[0].show()) | |
else: | |
print("No reply received.") |
ARP(注意 ARP 中的 hwsrc 需要再设置一次 mac,否则接收不到回包)
from scapy.all import * | |
eth_frame = Ether(src="3a:a0:e5:64:0f:e3", dst="ff:ff:ff:ff:ff:ff") | |
arp_packet = ARP(hwsrc="3a:a0:e5:64:0f:e3",op='is-at',psrc="10.0.0.2",pdst="10.0.0.3",hwdst="ff:ff:ff:ff:ff:ff") | |
packet = eth_frame/arp_packet | |
reply_packets = srp1(packet, timeout=3, iface="eth0") | |
if reply_packets: | |
print(reply_packets.show()) | |
else: | |
print("No reply received.") | |
# print(arp_mitm("10.0.0.3","10.0.0.2")) |
ARP 欺骗(直接伪造 ip 即可)
sendp(Ether(src=get_if_hwaddr("eth0"), dst="ff:ff:ff:ff:ff:ff") / ARP(op="is-at", psrc="10.0.0.2", hwsrc=get_if_hwaddr("eth0")), iface="eth0") |
差一个题,稍微复杂,大概知道怎么做但是晚点做吧…