数字中国2024决赛
PREFACE:随便看了看
# Hardtree
其实就是每个节点有左右两子树,一个值,通过 lr 选择左右子树达到终点,搜索即可
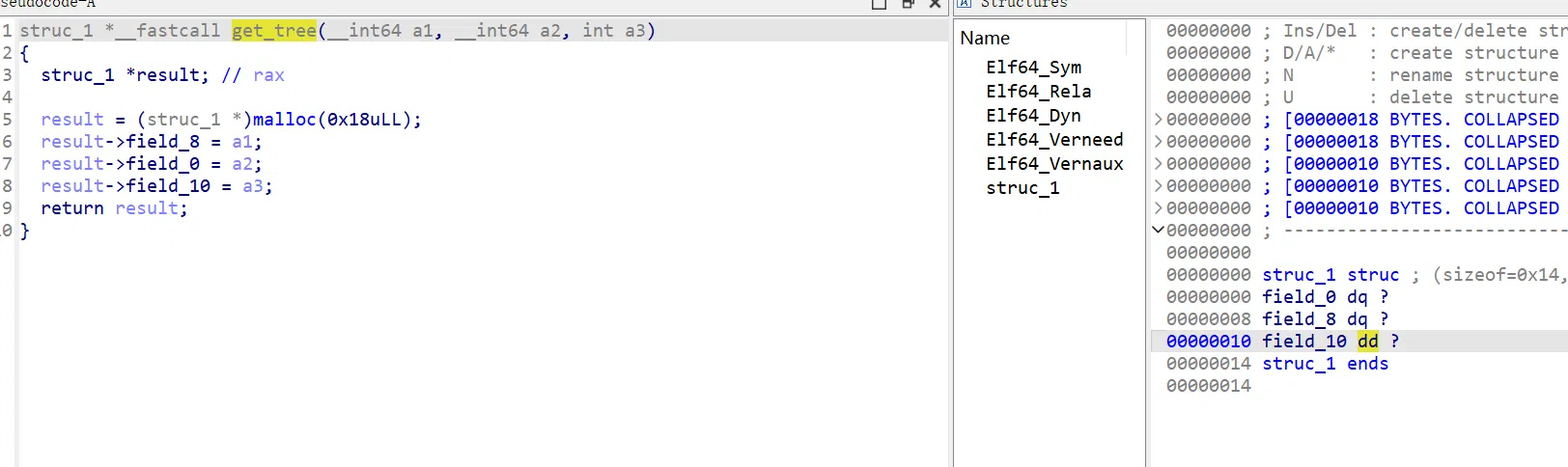
这里做后面解法,目前给出三种方法:
-
跑起来直接 dump 堆,这种是最简单的获取数据的方法
-
ida python 打印函数参数和返回值获取(这个不太行其实,数量太大速率提不上来)
-
unicorn 模拟,短时间也同样跑不出来,还是数据太长,而且栈爆了,不过思路是提供这么个思路
from unicorn import * | |
from unicorn.x86_const import * | |
from capstone import * | |
REAL_BASE_OFFSET = 0x400 | |
md = Cs(CS_ARCH_X86, CS_MODE_64) | |
lld = {} | |
left_son = 0 | |
right_son = 0 | |
value = 0 | |
def read(name): | |
with open(name,'rb') as f: | |
return f.read() | |
import random | |
def hookDbgPrint(mu,address,size,user_data): | |
global lld, left_son, right_son, value | |
code = mu.mem_read(address, size) | |
# for instruction in md.disasm(code, address): | |
# print("0x%x: %s %s" % (instruction.address, instruction.mnemonic, instruction.op_str)) | |
if (address == 0x130A): | |
left_son = mu.mem_read(mu.reg_read(UC_X86_REG_RDI), 32) | |
right_son = mu.mem_read(mu.reg_read(UC_X86_REG_RSI), 32) | |
value = mu.mem_read(mu.reg_read(UC_X86_REG_EDX), 16) | |
if (address == 0x132B): | |
mu.reg_write(UC_X86_REG_RAX,random.randint(0xeeeeee, 0xFFFFFF)) | |
self = mu.mem_read(mu.reg_read(UC_X86_REG_RAX), 32) | |
# print(self,left_son) | |
lld[bytes(self)] = [bytes(left_son),bytes(right_son),bytes(value)] | |
def hookSYS(mu,address,size,user_data): | |
code = mu.mem_read(address, size) | |
# print(code) | |
for instruction in md.disasm(code, address): | |
# print(type(instruction.mnemonic)) | |
if ('call' in instruction.mnemonic and '0x1110' in instruction.op_str): | |
# print('malloc hooked') | |
mu.reg_write(UC_X86_REG_RIP, address + 5) | |
def hookEND(mu : Uc,address,size,user_data): | |
global lld | |
if (address == 0x7522E8): | |
print("end") | |
with open('lld','w') as file: | |
file.write(str(lld)) | |
mu.emu_stop() | |
mu = Uc (UC_ARCH_X86, UC_MODE_64) | |
BASE = 0 | |
STACK_ADDR = 0x1000000 | |
STACK_SIZE = 0x1000*0x1000 | |
mu.mem_map(BASE, 0x1000*0x1000) | |
mu.mem_map(STACK_ADDR, STACK_SIZE) | |
mu.mem_write(BASE, read("./HardTree")) | |
mu.reg_write(UC_X86_REG_RBP, STACK_ADDR + STACK_SIZE // 2) | |
mu.reg_write(UC_X86_REG_RSP, STACK_ADDR + STACK_SIZE // 3) | |
mu.hook_add(UC_HOOK_CODE,hookDbgPrint) | |
mu.hook_add(UC_HOOK_CODE,hookEND) | |
mu.hook_add(UC_HOOK_CODE,hookSYS) | |
mu.emu_start(0x752427 , 0x75243A) |